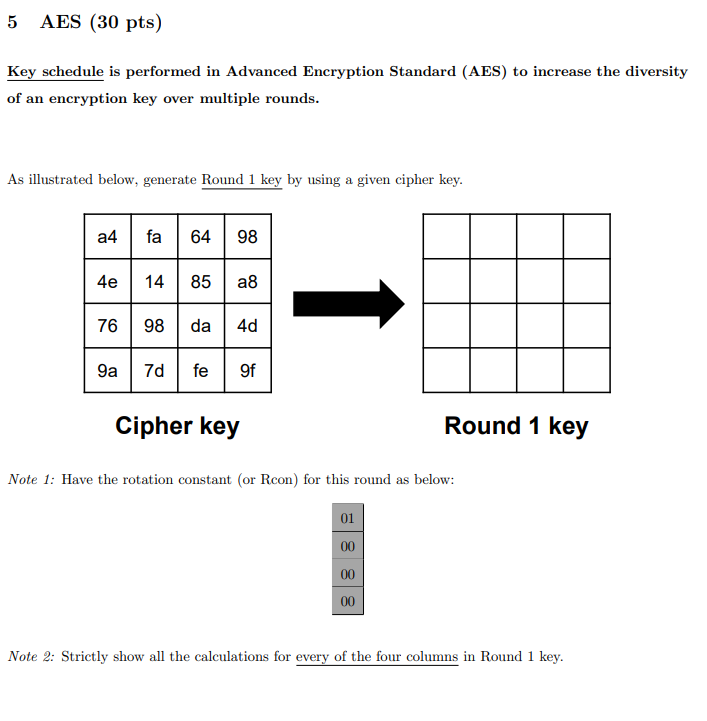
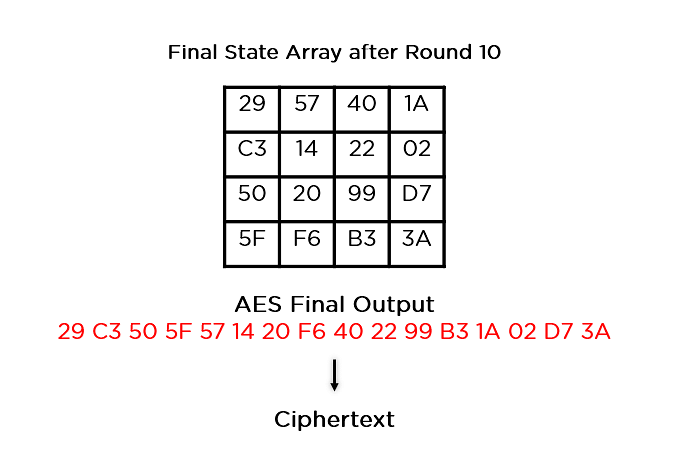
a): AES -Add Round Key B. Substitute Bytes: Substitute Byte is also... | Download Scientific Diagram
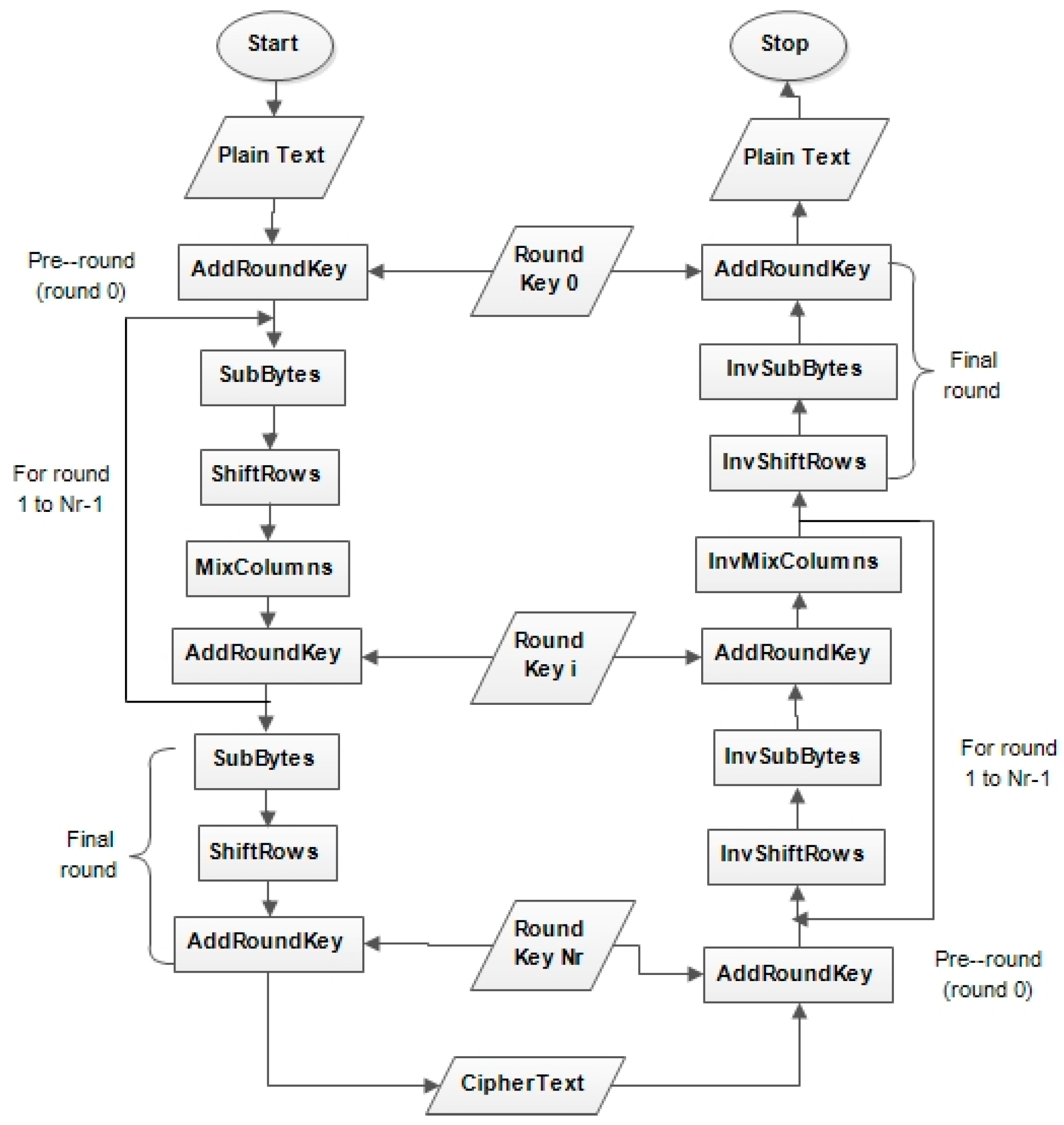
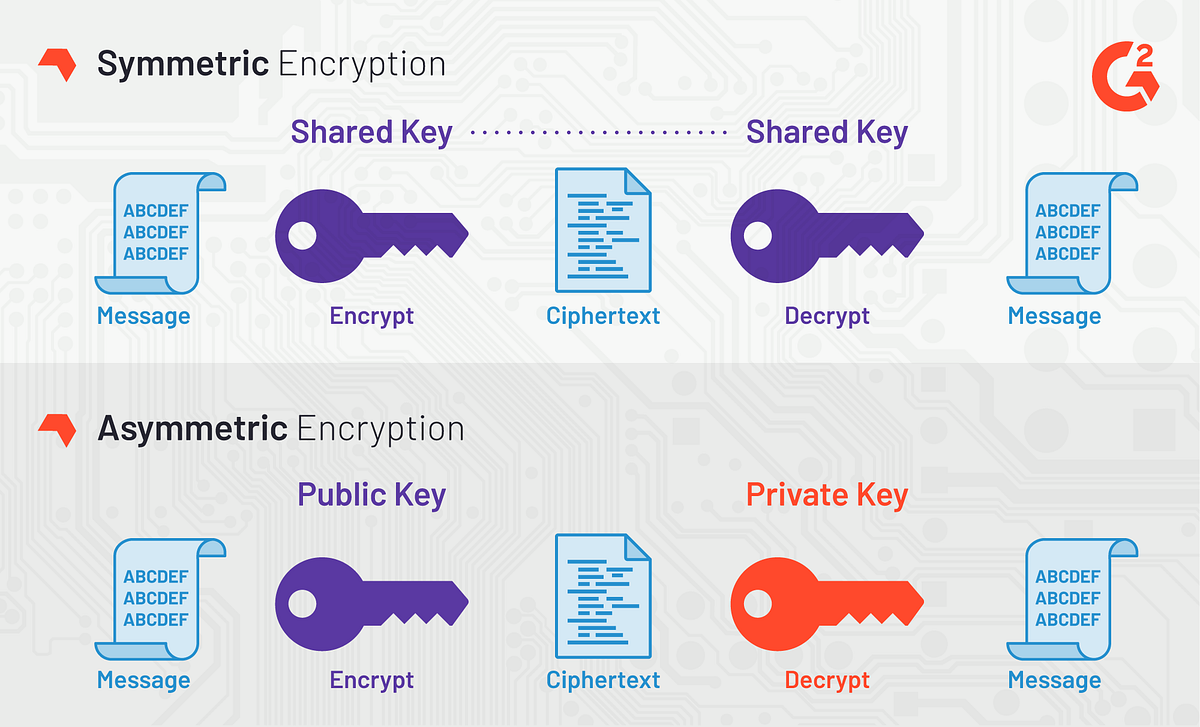
Symmetry | Free Full-Text | Modified Advanced Encryption Standard Algorithm for Information Security
![cryptanalysis - S-AES RC[i] Generation. Can someone explain how to generate the RC[i]s for these two problems I have? - Cryptography Stack Exchange cryptanalysis - S-AES RC[i] Generation. Can someone explain how to generate the RC[i]s for these two problems I have? - Cryptography Stack Exchange](https://i.stack.imgur.com/lKNyR.jpg)
cryptanalysis - S-AES RC[i] Generation. Can someone explain how to generate the RC[i]s for these two problems I have? - Cryptography Stack Exchange
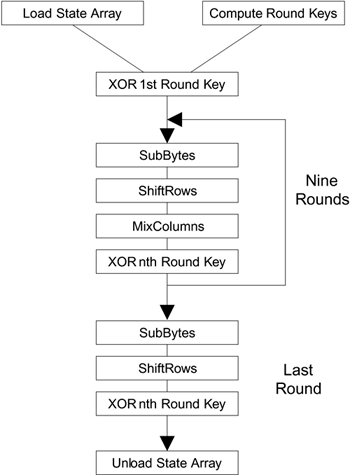
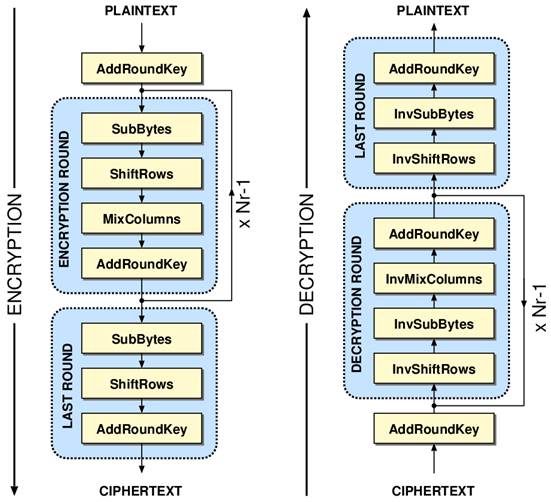
Steps in the AES Encryption Process :: Appendix A. Overview of the AES Block Cipher :: Appendixes :: 802.11 security. wi-fi protected access and 802.11i :: Networking :: eTutorials.org



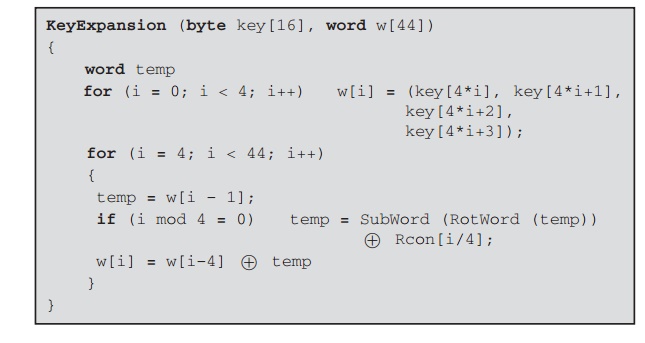
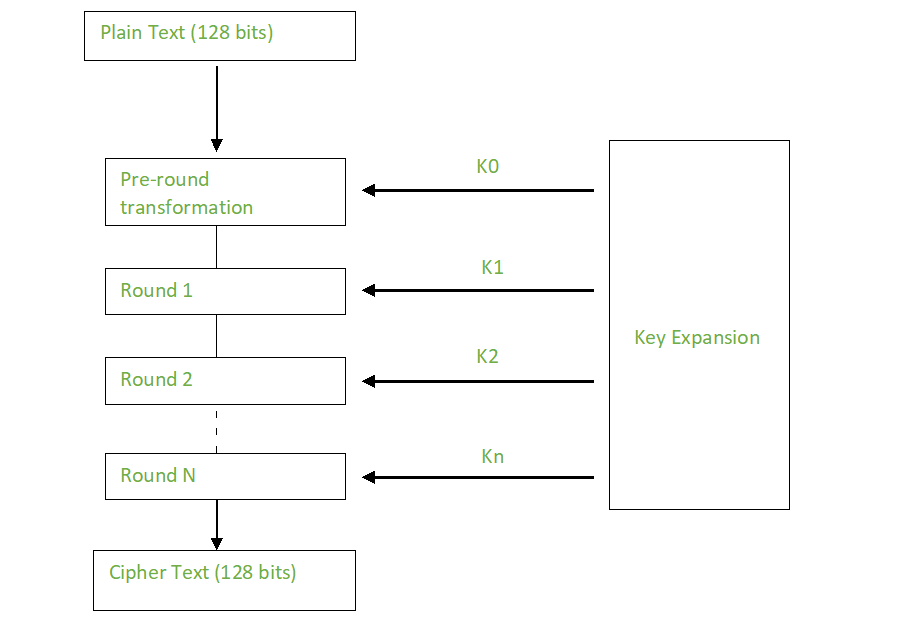
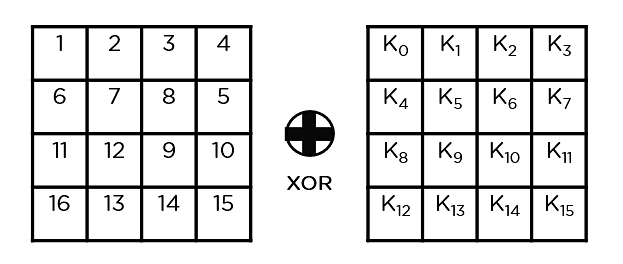



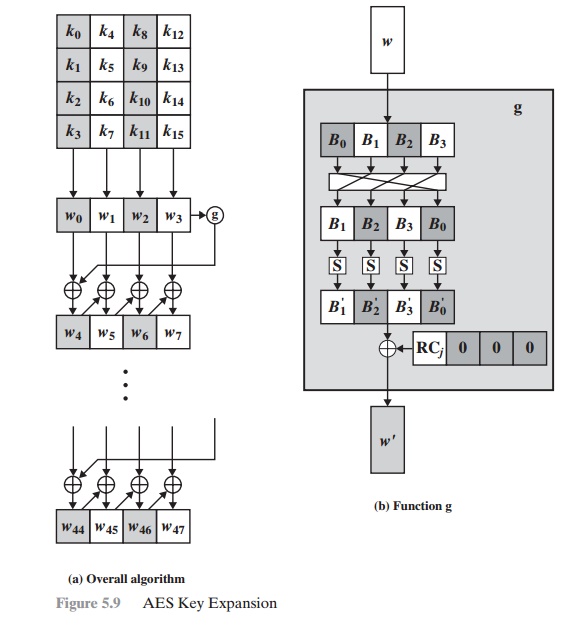

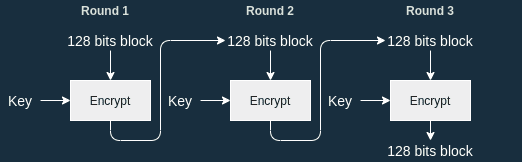
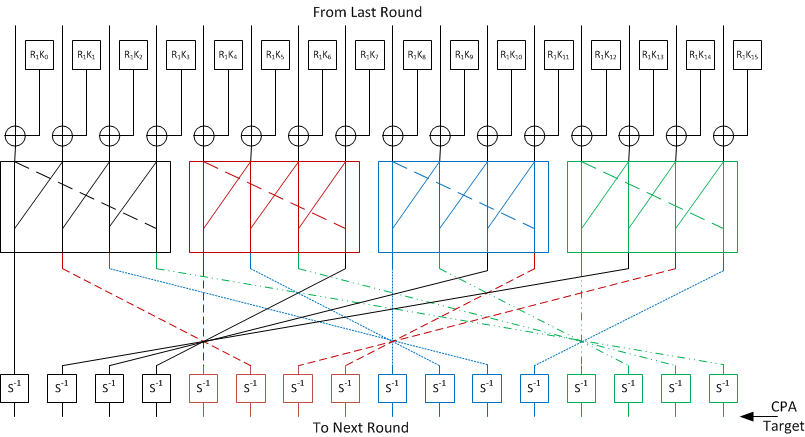


![What Is AES Encryption? [The Definitive Q&A Guide] What Is AES Encryption? [The Definitive Q&A Guide]](https://www.trentonsystems.com/hs-fs/hubfs/White%20and%20Yellow%20Simple%20Technology%20Keynote%20Video%20Presentation%20(6).png?width=690&name=White%20and%20Yellow%20Simple%20Technology%20Keynote%20Video%20Presentation%20(6).png)